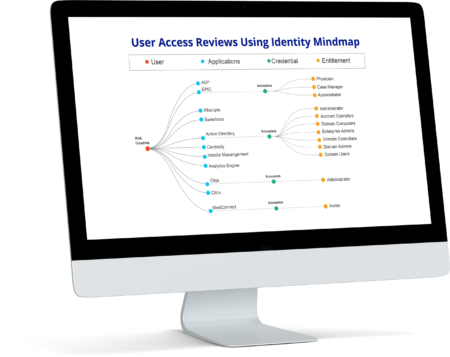
In today’s digital landscape, maintaining secure access to critical systems and sensitive data is paramount. User Access Reviews by Secure Ends offer a robust solution for businesses looking to enhance security, reduce unauthorized access, and comply with industry regulations. Implementing a structured user access review process ensures that only the right individuals have access to the right resources at the right time.
What Are User Access Reviews?
User Access Reviews (UAR) are periodic assessments conducted to verify and validate users’ access rights across an organization’s IT infrastructure. These reviews help organizations identify and remove excessive, outdated, or unauthorized permissions, thereby reducing the risk of data breaches and insider threats.
Why Choose User Access Reviews by Secure Ends?
Secure Ends provides a comprehensive and automated approach to User Access Reviews, ensuring efficiency, accuracy, and compliance with regulatory standards. Here’s why businesses should leverage Secure Ends for their access review needs:
1. Enhanced Security & Risk Reduction
Regular User Access Reviews by Secure Ends help detect and eliminate redundant or unauthorized access, minimizing security vulnerabilities. By ensuring that access privileges are granted based on business needs, organizations can effectively reduce insider threats and data breaches.
2. Regulatory Compliance
With increasing regulatory requirements such as GDPR, HIPAA, and SOX, organizations must implement stringent access controls. Secure Ends ensures that businesses meet compliance mandates by conducting thorough and documented access reviews.
3. Automation & Efficiency
Manual access reviews can be time-consuming and error-prone. Secure Ends offers an automated solution that simplifies the process, reducing human effort while ensuring accuracy and timely compliance.
4. Audit-Ready Reports
Secure Ends generates comprehensive audit reports, making it easier for organizations to demonstrate compliance to auditors and regulators. These reports provide clear insights into user permissions, access changes, and policy adherence.
5. Role-Based Access Controls (RBAC) & Least Privilege Enforcement
Secure Ends enables organizations to enforce role-based access controls (RBAC) and the principle of least privilege, ensuring that users have only the necessary access required for their roles.
Key Features of User Access Reviews by Secure Ends
– Automated Access Validation
Secure Ends automates the access review process, reducing administrative overhead and improving review accuracy.
– Customizable Review Policies
Organizations can define their own review policies, setting periodic access reviews based on role, department, or compliance requirements.
– User-Friendly Dashboard
A centralized dashboard provides visibility into all user access data, allowing administrators to take swift action on access-related risks.
– Integration with IAM & IT Systems
Secure Ends seamlessly integrates with Identity and Access Management (IAM) solutions, cloud applications, and on-premises IT systems for a holistic access review process.
How to Implement User Access Reviews with Secure Ends?
Implementing User Access Reviews by Secure Ends is a straightforward process:
-
Assess Current Access Controls – Review existing access permissions and identify risks.
-
Define Review Policies – Set parameters for periodic access reviews based on security and compliance needs.
-
Automate the Review Process – Utilize Secure Ends’ automation tools for efficient validation.
-
Analyze & Take Action – Address any unauthorized or unnecessary access permissions.
-
Generate Compliance Reports – Maintain detailed records for audit and regulatory requirements.
Conclusion
User Access Reviews by Secure Ends provide organizations with a proactive approach to managing user permissions, mitigating security risks, and ensuring compliance. By automating and streamlining the access review process, businesses can significantly reduce unauthorized access and improve overall security posture.
Secure your organization today with User Access Reviews by Secure Ends—your trusted partner in access management and compliance.




Leave a Reply